Enable the decryption feature on the Big-IP:
tmsh modify sys db tcpdump.sslprovider value enable
Run the tcpdump with the “ssl” flag:
tcpdump -nni 0.0:nnnp -s0 -w /var/tmp/dump.pcap --f5 ssl
Now get the dump.pcap file onto a device with tshark installed and strip out the PMS information:
tshark -r dump.pcap -Y "f5ethtrailer.tls.keylog" -T fields -e f5ethtrailer.tls.keylog | tr , '\n' > keylog.txt
I'm not sure why you can't do it on the Big-IP but it didn't work for me.
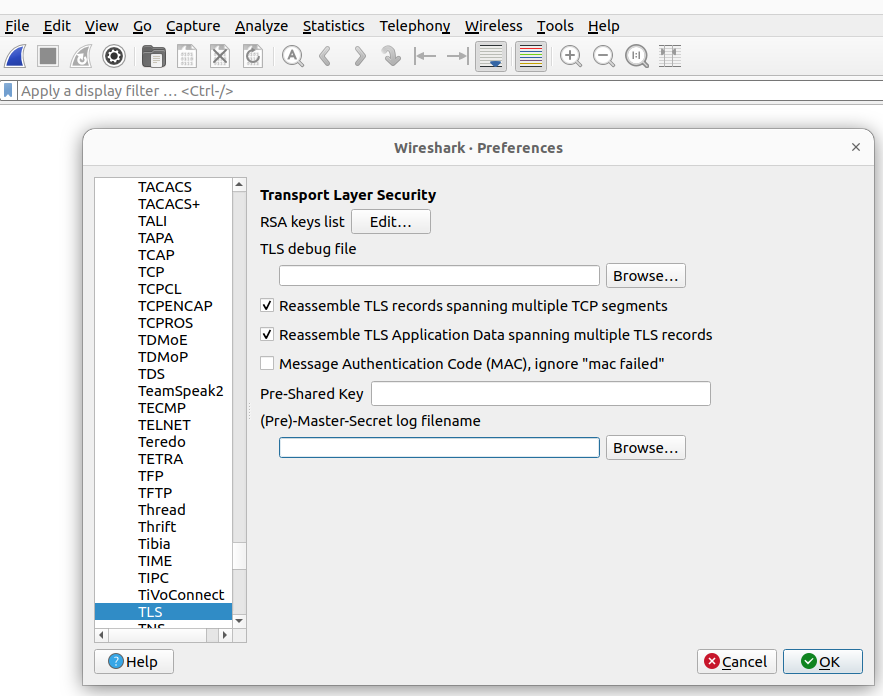
Now open Wireshark and go to “Edit → Preferences → Protocols → TLS”. Find the field called “(Pre)-Master-Secret log filename” and click “Browse”. Locate your keylog.txt file and select it.
Next open up the dump.pcap tcpdump file and you should now be able to see decrypted traffic.
If you do not find the traffic decrypted it could be that you have captured the traffic midstream, before the master secret was made. To overcome this you just need to make sure you run tcpdump before the connection is created between whatever you are trying to decrypt then you should get all the information needed in the tcpdump file.
REMEMBER to delete all the tcpdump files afterwords, it could contain passwords or other sensitive information you don't want to get in the wrong hands.
